7. Advanced capture options
Until now we saw how to create simple capture using either the WebUI or the command line. This part will be a tour of the "advanced" capture options.
BPF filtering
First let start our lab with the usual Vagrant deployment.
git clone https://github.com/skydive-project/skydive
cd skydive/contrib/vagrant
vagrant upWhile we create a capture we can decide to capture everything or just a part of
the traffic leveraging BPF filtering via the
PCAP filter syntax.
Filtering ICMPv4 packets with the WebUI :
Or with the command line :
export SKYDIVE_ANALYZERS=192.168.50.10:8082
skydive client capture create --gremlin "G.V().Has('Name', 'eth0')" --bpf "icmp"Capture types
Skydive supports multiple ways to capture packets. By default the most adapted type
is chosen automatically by Skydive. For example if you start a capture on a Open vSwitch
bridge, the sFlow type will be used.
Here the list of the currently supported capture types :
- AFPACKET : MMap’d AF_PACKET socket (default).
- PCAP : Packet Capture library based.
- PCAP Socket : open a TCP port accepting PCAP file format. Useful to inject already captured traffic to Skydive.
- sFlow : implement a sFlow agent. It opens a UDP port reading
sFlowframes. Useful to sendsFlowtraffic from external resources to Skydive. - eBPF : in Kernel lightweight capture solution.
- OvsMirror : leverages Open vSwitch port mirroring.
Capture type has to be specified during the capture creation.
skydive client capture create --gremlin "G.V().Has('Name', 'eth0')" --type pcapKeep original packets
While Skydive analyzes the packets to build flows, keeping them in flow tables,
it is possible to keep the original packets attached to flows. This allows us to
download them as PCAP file. That way Skydive acts as a distributed tcpdump.
The following video shows how to start a such capture and how to retrieve the PCAP file.
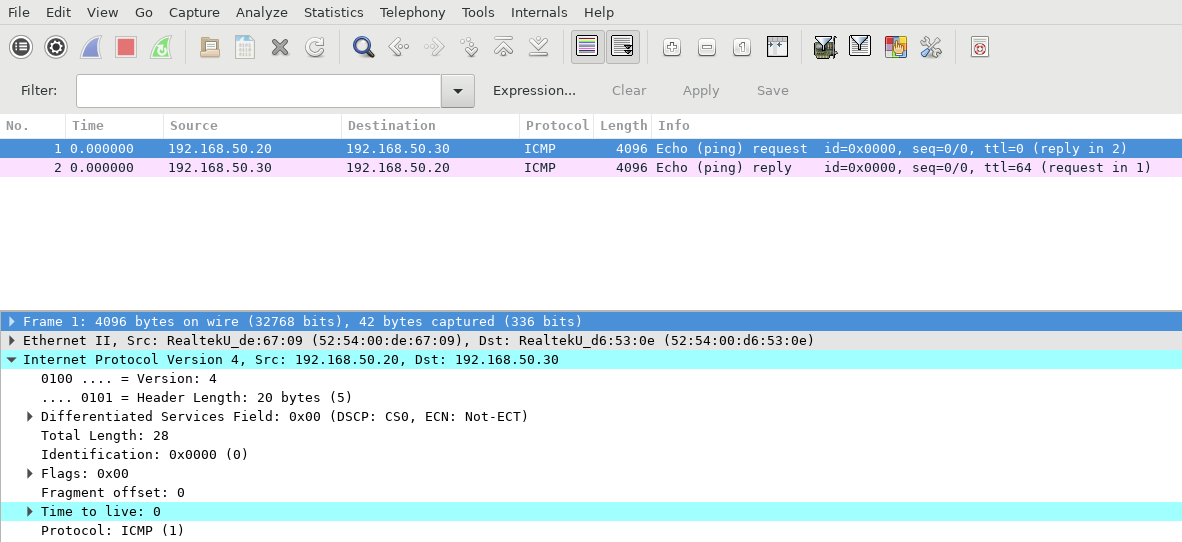
Clicking on the download icon we get the file which opened with Wireshark gives :
We can of course use the command line to create the capture, here limiting to 5 raw packets per flow.
skydive client capture create --gremlin "G.V().Has('Name', 'eth0')" --rawpacket-limit 5To get the PCAP file we just need to use the Gremlin step RawPackets specifying the
output format.
skydive client query "G.At('-1s', 1000).Flows().Has('Application', 'ICMPv4').RawPackets()" \
--format pcap > icmp.pcapThis searches flows with the ICMPv4 protocol since the last 1000 seconds
exporting their RawPackets in the icmp.pcap file.
tcpdump -qns 0 -r icmp.pcap
reading from file icmp.pcap, link-type EN10MB (Ethernet)
15:43:02.626000 IP 192.168.50.20 > 192.168.50.30: ICMP echo request, id 0, seq 0, length 8
15:43:02.626000 IP 192.168.50.30 > 192.168.50.20: ICMP echo reply, id 0, seq 0, length 8
15:43:02.626000 IP 192.168.50.20 > 192.168.50.30: ICMP echo request, id 0, seq 0, length 8
15:43:02.626000 IP 192.168.50.30 > 192.168.50.20: ICMP echo reply, id 0, seq 0, length 8It gaves us 4 packets, 2 per capture from 2 different hosts.
BPF, RawPackets captures and the query language makes Skydive a really powerful
distributed troubleshooting tool.